Security
In the previous articles, we showed how to perform packet marking in nftables based on geoip source ip addresses
and also how to log traffic to external files
.
Today we will show how to mark packets based on which continent they come from.
The principle is that we first mark packets based on the source IP address so that we know which countries they are coming from. And then we'll find out which continent the state is on.
We'll learn how we can block traffic originated from specific country or continent IPs using GeoIP database and linux nftables . This article describes the configuration for debian linux distros. nftables is the new packet classification framework that intends to replaces the existing {ip,ip6,arp,eb}_tables infrastructure. In a nutshell:
- It is available in Linux kernels >= 3.13
- It comes with a new command line utility nft whose syntax is different to iptables.
- It also comes with a compatibility layer that allows you to run iptables commands over the new nftables kernel framework.
- It provides generic set infrastructure that allows you to construct maps and concatenation. You can use this new feature to arrange your ruleset in multidimensional tree which drastically reduces the number of rules that need to be inspected until you find the final action on the packet.
I assume you have at least basic experience with the nftables configuration.
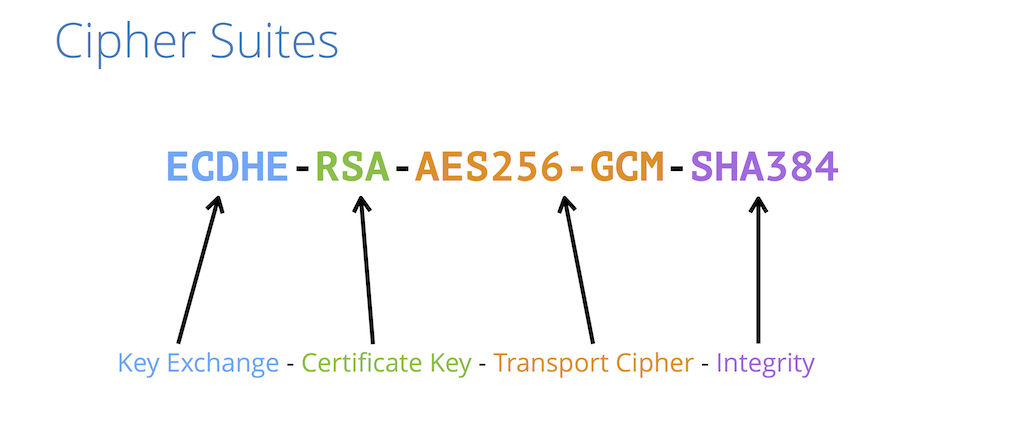
What is a cipher suite?
Cipher suites decide how secure, compatible and fast your HTTPS website is. A cipher suite is a set of information that helps determine how your web server will communicate secure data over HTTPS.
A web server uses certain protocols and algorithms to determine how it will secure your web traffic. These are the ingredients of a secure connection. A cipher suite is essentially a list of those ingredients.