Understanding Key Differences Between FTP, FTPS and SFTP
Understanding Key Differences Between FTP, FTPS and SFTP
Perhaps the most common protocols used in file transfer today are FTP, FTPS and SFTP. While the acronyms for these protocols are similar, there are some key differences among them, in particular how data are exchanged, the level of security provided and firewall considerations. Learning these key differences can help you when choosing a file transfer protocol or troubleshooting common connection issues.
1. FTP
The FTP (File Transfer Protocol) protocol has been around for quite some time. The File Transfer Protocol (FTP) is a standard network protocol used for the transfer of computer files between a client and server on a computer network .
1.1 Data Exchange
The FTP protocol exchanges data using two separate channels known as the ftp command channel and ftp data channel.
The command channel typically runs on server port 21 and is responsible for accepting client connections and handling the exchange of simple commands between an FTP client and server. The USER and PASS commands used for authenticating an FTP user are examples of commands that are exchanged on the command channel. The command channel remains open until the client sends the QUIT command to disconnect, or the server forcibly disconnects the client due to inactivity or other reason.
The data channel, runs using on-demand temporary ports listening on the server in passive mode or on the client in active mode and is responsible for exchanging data in the form of directory listings and file transfers. The LIST, STOR and RETR commands used for getting a server directory listing, uploading a file and downloading a file are examples of commands (sent using the command channel) that open a data channel. Unlike the command channel which remains open during the entire FTP session, the data channel is closed once the transfer of data is complete. In order to handle concurrent file transfers or directory listings a range of data channel ports must be used.
1.2 Security
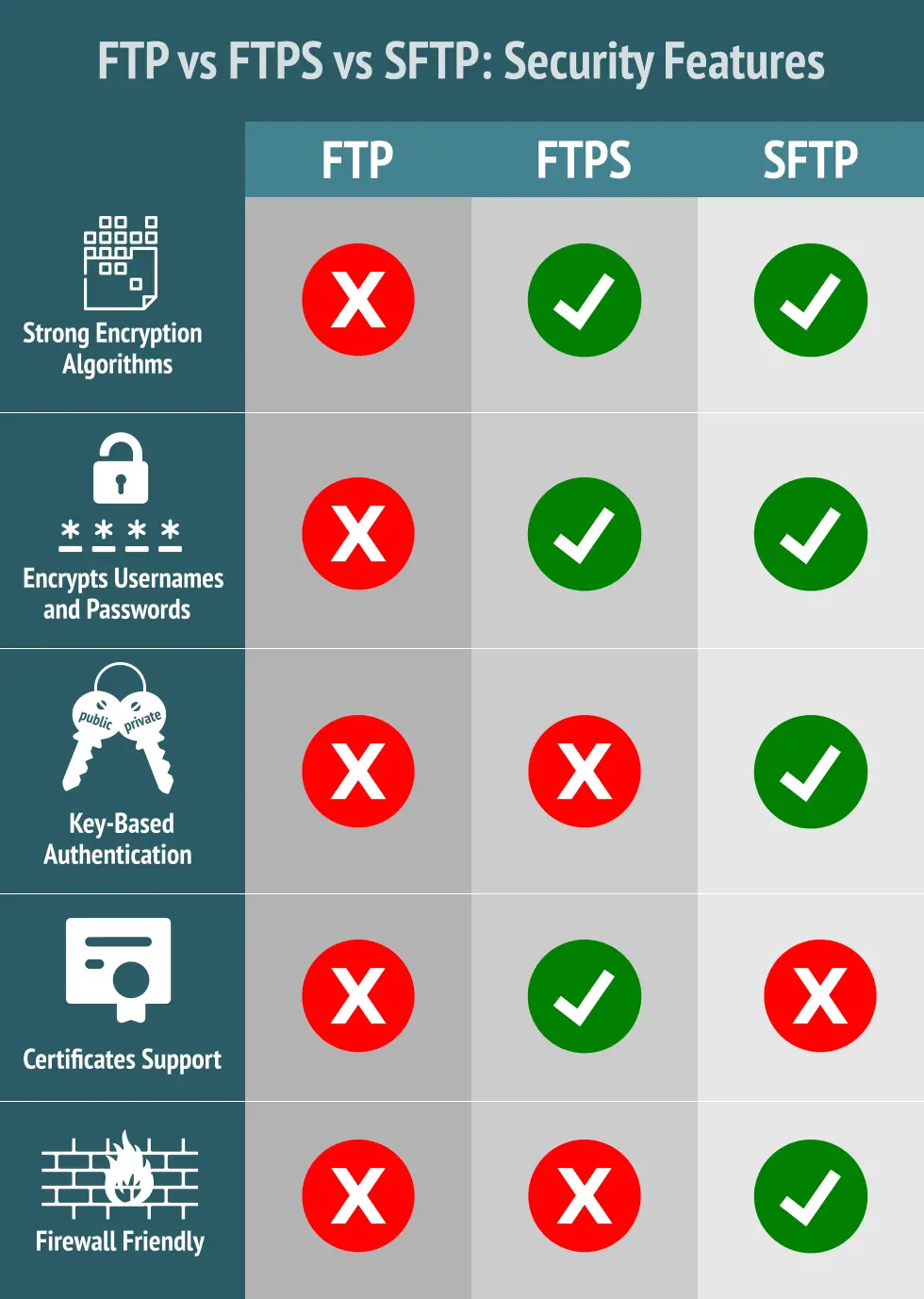
Using FTP both the command and data channels are unencrypted. Any data sent over these channels can be intercepted and read. One common exploit that takes advantage of this particular vulnerability is the man-in-the-middle attack using ARP poisoning and a packet sniffer .
1.3 Firewall
Server - Allow inbound connections on port 21. Define passive port range (e.g. 2000-2500) for file transfers and directory listings and allow inbound connections on passive port range. Consult your server documentation for instructions on how to set a passive port range.
Client - Allow outbound connections to port 21 and passive port range defined by server.
Many firewall issues encountered when using FTP are caused by a poor understanding of FTP's two modes: the active mode and the passive mode. The settings you will ahve to make on your server-side firewall or your client-side firewall will largely depend on which mode you choose. To avoid these issues, we suggest you take time for a deeper discussion on active and passive FTP .
2. FTPS
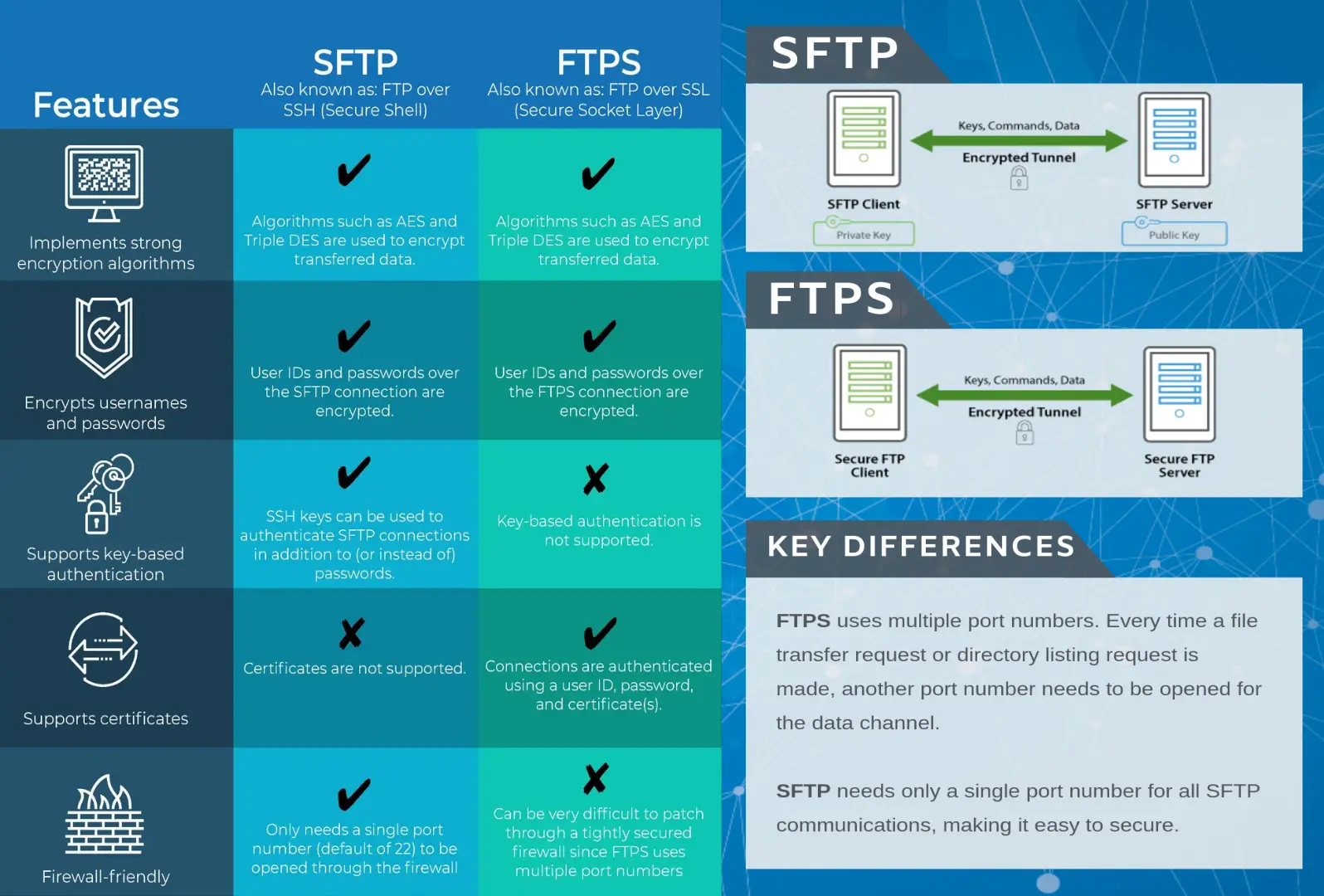
When the FTP protocol was initially drafted security was not a concern. Since then many things have changed and sending data over any public network without encryption is considered very risky and in some cases prohibited. In order to address this issue a set of security extensions to the original FTP protocol were proposed in RFC 2228 that protect FTP data as it travels over the network using SSL encryption.
2.1 Security
Secure variants of FTP include FTPS Implicit SSL and FTPS Explicit SSL. Both utilize SSL
encryption.
2.1.1 FTPS Implicit SSL
As its name implies, implicit SSL is a type of FTPS connection wherein SSL encryption is implied. As soon as a connection is established between the FTPS client and your managed file transfer server, both command (a.k.a. control) and data channels will be automatically protected with SSL encryption.
In implicit SSL mode a required SSL session is established between client and server before any data is exchanged. As it's name suggests, the use of SSL is implied and any connection attempt made by a client without using SSL are refused by the server. FTPS implicit SSL services generally run on port 990. Although still in use today, FTPS Implicit SSL is considered by many to be obsolete in favor of FTPS Explicit SSL.
Implicit SSL is ideal if you really want full encryption for your entire FTP connection from the start of the session. However, since encryption always consumes more bandwidth and computational resources, there may be instances when you'll want to encrypt only one channel.
For instance, if the files your users normally upload to your managed file transfer server don't contain confidential information, then the only things you will want to encrypt are the usernames and passwords that get submitted during authentication. Since user credentials are sent via the command channel, then that's the only channel you would need to encrypt.
But then you can't do that with Implicit SSL. Implicit SSL always encrypts both the command and data channels.
2.1.2 FTPS Explicit SSL
For the situation described above (encrypt only user credentials), a better choice would be Explicit SSL. With Explicit SSL, you're allowed to choose which channel to encrypt. You can even choose to revert back to regular (unencrypted) FTP and not encrypt any channel at all. Explicit SSL runs over port 21, which is the same port used by regular FTP, making it easy for your server to cater to both clients that support FTPS and those that only support regular FTP.
In explicit SSL mode the client and server negotiate the level of protection used. This is very useful in that the server can support both unencrypted FTP and encrypted FTPS sessions on a single port. In an explicit SSL session the client first establishes an unencrypted connection to the FTP service. Prior to sending user credentials, the client requests that the server switch the command channel to an SSL encrypted channel by sending the AUTH TLS or AUTH SSL command. Upon successful setup of the SSL channel the client then sends user credentials to the FTP server. These credentials along with any other commands sent to server during the FTP session are automatically encrypted by the SSL channel. Similar to the way in which the command channel may be protected, the level of protection used on the data channel is negotiated between the client and server using the PROT command.
2.2 Firewall
Server - Allow inbound connections on port 21 and/or 990.Define passive port range
(e.g. 2000-2500) for file transfers and directory listings and allow inbound connections on passive port range. Consult your server documentation for instructions on how to set a passive port range.
Client - Allow outbound connections to port 21 and passive port range
defined by server.
| Implicit FTPS | Explicit FTPS |
|---|---|
| Commands and data channels are encrypted at all times. | The client request security from the FTPS server directly, which is entirely optional. |
| SSL/TLS encryption is implemented at the beginning of the session | Or the FTPS server can either allow the client to continue in unsecure mode or limit the connection. |
| A secure FTPS is mandatory | Used when the requirement is to secure only the command channel (carrying command and user authentication) and not the data channel. (carrying non-confidential data) |
| Defines a specific port for the clients to use for secure connections (default port 990) | The default port used by the server to communicate with clients is port 21 |
| Non-FTPS clients not allowed to communicate with the FTPS server | Allow the client to achieve increased security when needed and more speed when security is less of an issue |
RECOMMENDED |
FLEXIBLE |
| Dis: Consumes more Bandwitch and computational resources because encryption happens in both the command and data channel | Dis: Allow both unsecure and secure FTPS clients |
3. SFTP
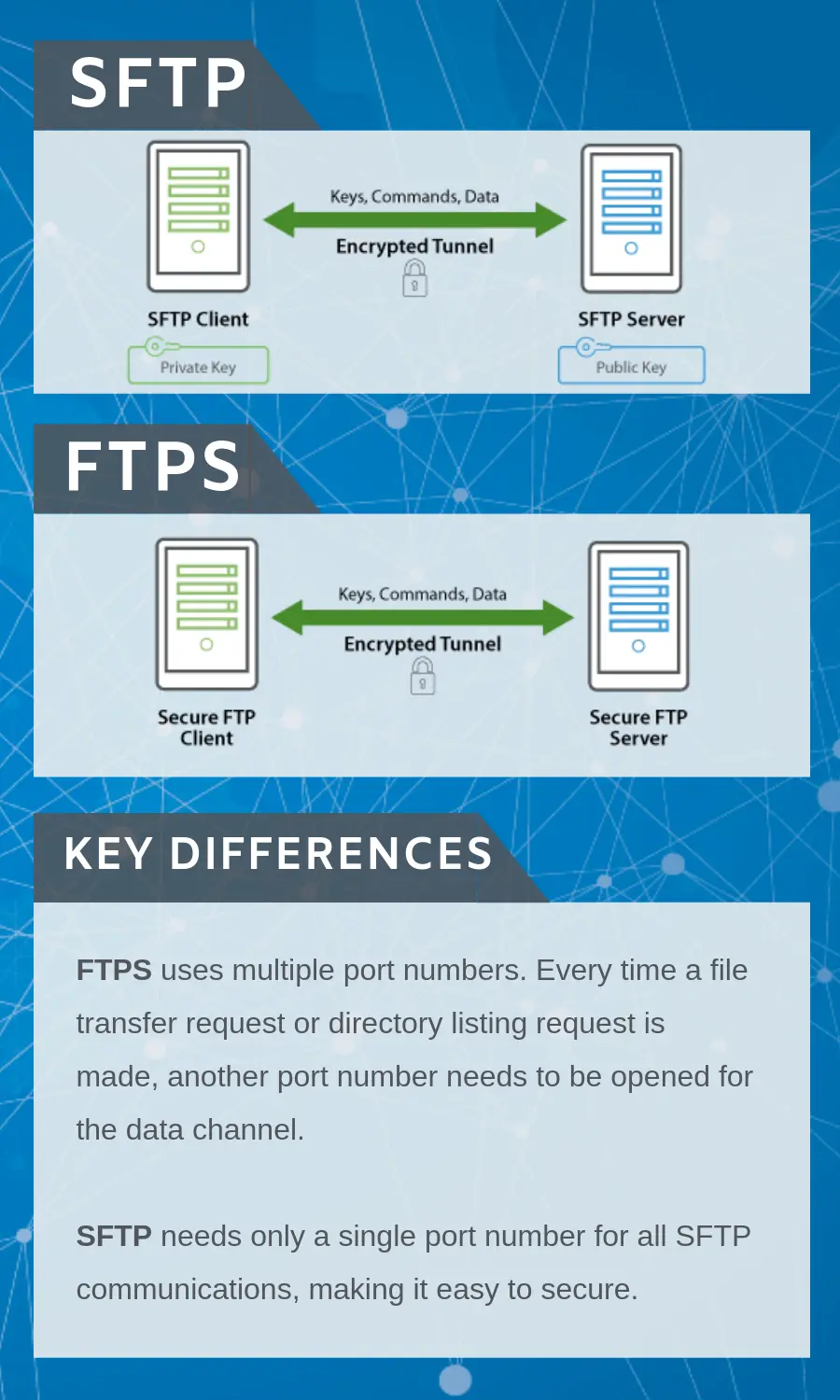
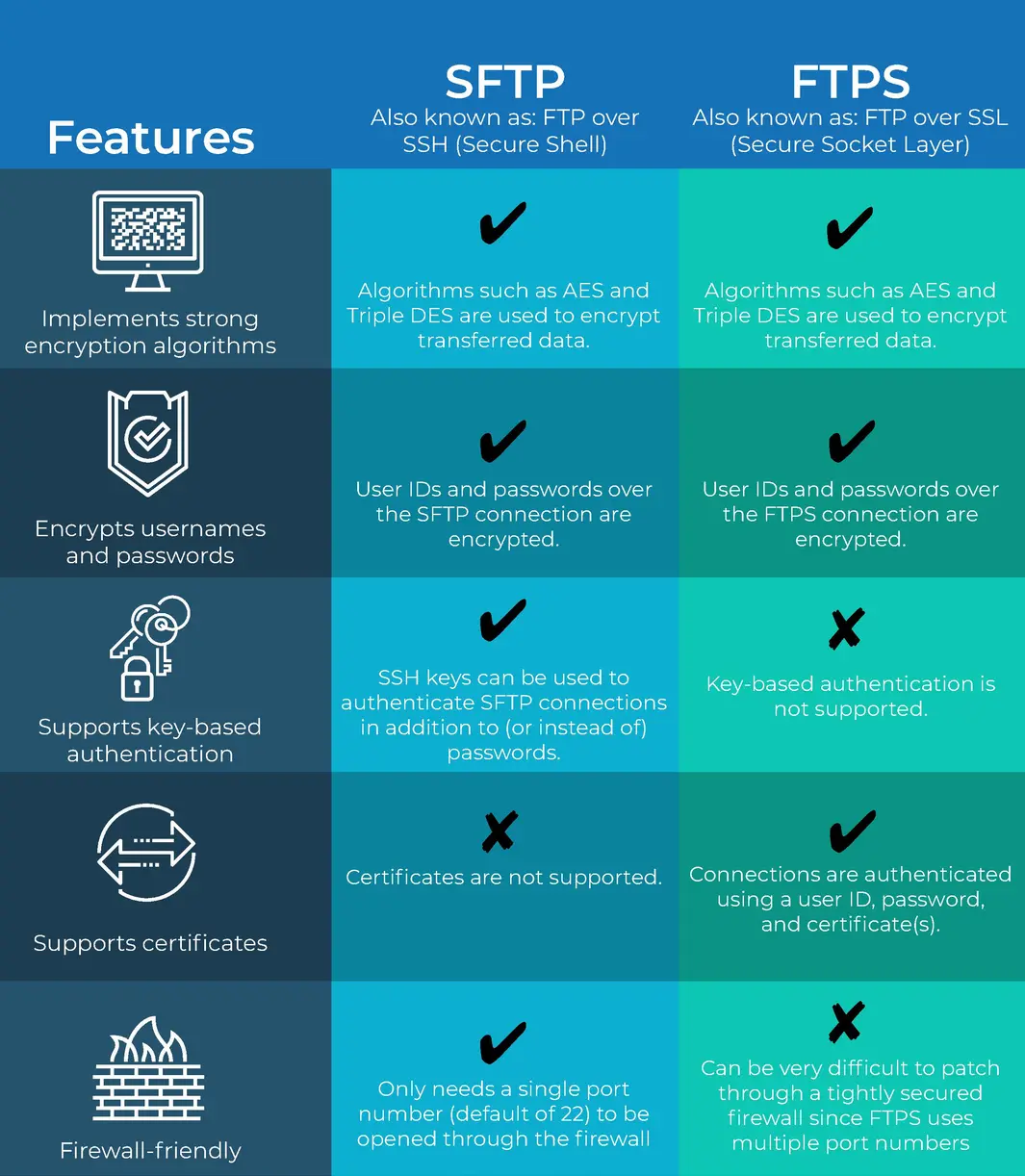
SFTP is often confused with FTPS and vice-versa even though these protocols share nothing in common except their ability to securely transfer files. SFTP is actually based on the SSH (Secure Shell) protocol which is best known for it's use in providing secure access to shell accounts on remote servers.
SFTP Data Exchange
Unlike FTP and FTPS , SFTP does not utilize separate command and data channels. Both data and commands are transferred in specially formatted packets via a single connection.
SFTP Security
All data sent between client and server is encrypted using an agreed upon encryption cipher. SFTP sessions can also be further protected through the use of public and private keys, which offer an alternative form of authentication known as public key authentication. This can be used as an alternative to or in conjunction with the traditional form of authentication of usernames and passwords.
SFTP Firewall Config
Server - Allow inbound connections on port e.g. 22.
Client - Allow outbound connections to port e.g. 22.