Active and Passive FTP Simplified - Understanding FTP Ports

FTP (File transfer protocol) is well known when it comes to transferring files between the client and the server over a network. There are two types of voice namely: Active and Passive. In this article the focus will be on Active and Passive FTP and their features, and application.
Active and Passive FTP Simplified - Understanding FTP Ports
If a client encounters problems when connecting to your FTP server
, one of the first things you might want to check is your FTP data transfer mode
. Depending on certain network configurations, this mode should be set to either active or passive. In this post, you’ll understand the salient points of active and passive FTP and learn how to avoid connectivity issues associated with them.
Before we talk about which mode is best for what scenario, let’s first cover one important topic: the two channels of an FTP session.Before we talk about which mode is best for what scenario, let’s first cover one important topic: the two channels of an FTP session.
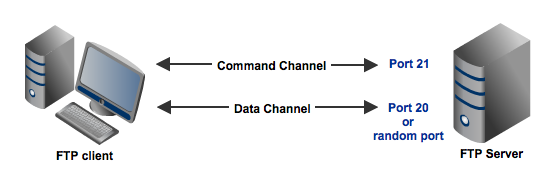
FTP command channel and data channel
A typical FTP session operates using two channels: a command (or control) channel and a data channel. As their names imply, the command channel is used for transmitting commands as well as replies to those commands, while the data channel is used for transferring data.
Unless you configure your FTP server differently, you will normally set your command channel to use port 21. The port you'll use for the data channel, on the other hand, can differ depending on which data transfer mode you choose. If you choose active mode, then the data channel will normally be port 20. But if you choose passive mode, then the port that will be used will be a random port.
summary:
FTP uses two communication paths (also known as “channels”) in order to accomplish its goal of transferring files from one location to another.
- Command Channel: Used to send FTP commands back and forth from the client and server. This connection is commonly made to port 21 of the server.
- Data Channel: Used to transmit the raw data of the files being sent. The server port used for this channel depends largely on what communication mode is being used, Active or Passive.
The default mode in FTP is Active mode
Active mode FTP
Among the two modes, Active mode is the older one. It was the mode introduced in the early days of computing when mainframes were more common and attacks to information security were not as prevalent.
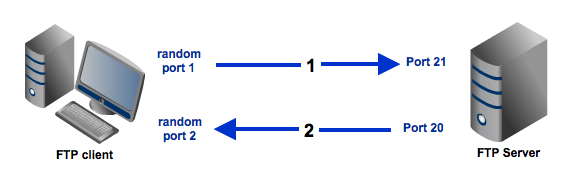
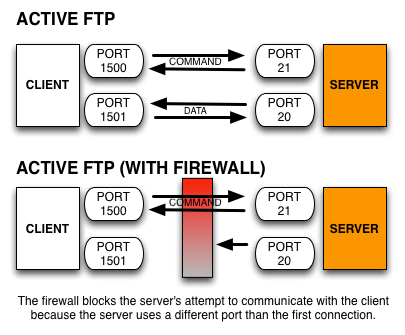
Here's a simplified explanation on how an active mode connection is carried out, summarized in two steps. Some relevant steps (e.g. ACK replies) have been omitted to simplify things.
- A user connects from a random port on a file transfer client to port 21 on the server. It sends the PORT command, specifying what client-side port the server should connect to. This port will be used later on for the data channel and is different from the port used in this step for the command channel.
- The server connects from port 20 to the client port designated for the data channel. Once connection is established, file transfers are then made through these client and server ports.
Passive mode FTP
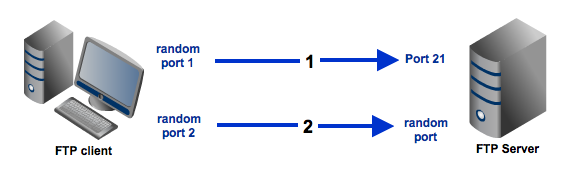
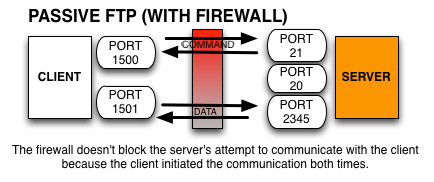
In passive mode, the client still initiates a command channel connection to the server. However, instead of sending the PORT command, it sends the PASV command, which is basically a request for a server port to connect to for data transmission. When the FTP server replies, it indicates what port number it has opened for the ensuing data transfer.
Here's how passive mode works in a nutshell:
- The client connects from a random port to port 21 on the server and issues the PASV command. The server replies, indicating which (random) port it has opened for data transfer.
- The client connects from another random port to the random port specified in the server's response. Once connection is established, data transfers are made through these client and server ports.
Active mode vs Passive mode - which is more suitable for you?
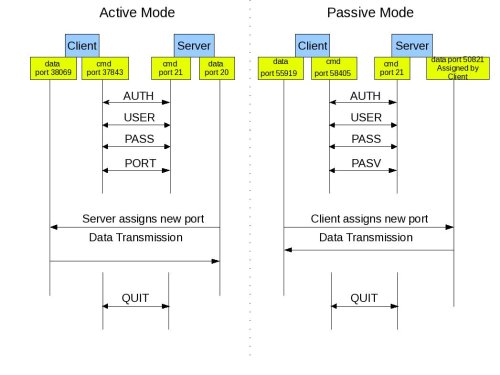
There's a reason why I opted to simplify those two diagrams above. I wanted to focus on the main difference between active mode and passive mode FTP data transfers. If you compare those two diagrams, one of the things that should really stand out are the opposing directions at which the second arrows (which also represent the data channels) are pointing to.
In this section, we'll focus on those second arrows and the ports associated with them.
-
In the active mode, the second arrow is pointing to the client. Meaning, the client initially specifies which client-side port it has opened up for the data channel, and the server initiates the connection.
-
By contrast, in the passive mode, the second arrow is pointing to the server. Here, the server specifies which server-side port the client should connect to and the client initiates the connection.
Active vs Passive FTP
Server initiates the connection in theactive mode. By contrast, client initiates the connection in the passive mode
There shouldn't be any problem had there not been any firewalls in existence. But threats to information security are on the rise and hence the presence of firewalls is almost always a given. In most cases, clients are located behind a firewall or a NAT (which basically functions like a firewall). In such cases, only a select number of predefined ports are going to be accessible from the outside.
Active mode with NAT and Firewall
Remember that in an active mode configuration, the server will attempt to connect to a random client-side port. So chances are, that port wouldn't be one of those predefined ports. As a result, an attempt to connect to it will be blocked by the firewall and no connection will be established.
Passive mode with NAT and Firewall
In this particular scenario, a passive configuration will not pose a problem. That's because the client will be the one initiating the connection, something that a client-side firewall won't have any problem with.
Security considerations when setting up passive FTP
As explained earlier, if you're administering an FTP server, it would be best for you to configure your server to support passive mode FTP. However, you should bear in mind that in doing so, you would be making your system more vulnerable to attacks. Remember that, in passive mode, clients are supposed to connect to random server ports.
Thus, to support this mode, not only should your server have to have multiple ports available, your firewall should also allow connections to all those ports to pass through!
But then the more open ports you have, the more there will be to exploit. To mitigate the risks, a good solution would be to specify a range of ports on your server and then to allow only that range of ports on your firewall.
How wide should the passive port range be?
The number of ports you need to specify in passive FTP largely depends on the number of concurrent connections/file transfers you expect to have. However, although, say, 100 concurrent file transfers would only require 100 open ports on the server, always remember that what most people consider as a "single file transfer" may actually consist of more than one. Let me explain.
For a typical end user, everything he downloads or uploads between the time he logs in to the FTP server and the time he logs out, is just part of a single FTP file transfer. That's not true. Each file transmitted during that entire login session will actually require at least one port. So if 10 files are downloaded, then 10 ports are used. That's not all.
Some clients now use multiple connections when uploading files. For example, if a client has 100 files to upload, it might spawn 5 separate sessions to make the upload go faster. The result is that a single client may have 5 open passive connections at a time.
So, when deciding how many passive ports you want to open you need to consider that a single client may actually open multiple concurrent passive connections. While there are no hard and fast rules dictating the number of ports that should comprise a port range, you will really want to project your maximum number of concurrent users and allocate a sizable allowance based on that.
Summary:
The difference between active FTP and passive FTP modes lies in how connections are made. In active mode, the client initiates the connection with a PORT command, making the server connect back for data. In passive mode, the client uses a PASV command, gets a server port, and starts the data transfer connection.
An easy way to remember which mode is which is to associate the mode with how the server behaves.
- Active FTP Mode: The server actively makes the data channel connection to the client.
- Passive FTP Mode: The server behaves passively and waits for the client to connect to it.